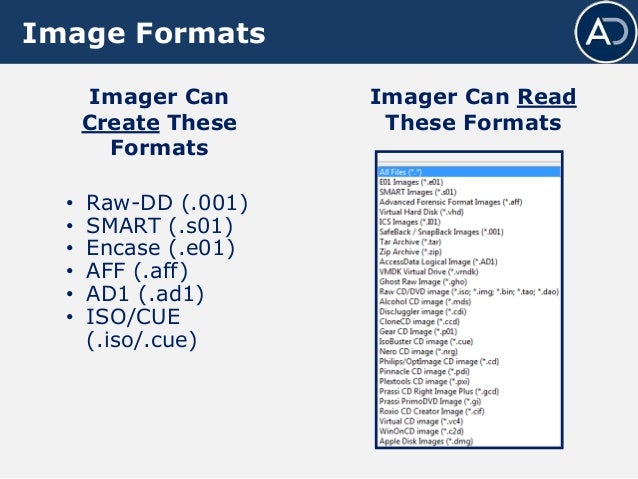
NTFS (and NTFS compressed) HFS, HFS, and HFSX FTK Imager can create evidence files of the following formats E01, S01, and L01 AFF AD1 RAW/DD FTK Imager read formats—in the following screenshot you can see all the formats that FTK Imager supports to Here is the majority of the FTK Imager Helpfile which you can get by simply executing the precompiled binary Usage ftkimager source dest_file options source can specify a block device, a supported image file, or `' for stdin if dest_file is specified, proper extension for image type will be appendedA Hard Drive that you would like to create an image of Method Step 1 Download and install the FTK imager on your machine Step 2 Click and open the FTK Imager, once it is installed You should be greeted with the FTK Imager

Ppt Ftk Imager 2 6 1 Powerpoint Presentation Free Download Id
Ftk imager lite can produce all the following image formats except which one
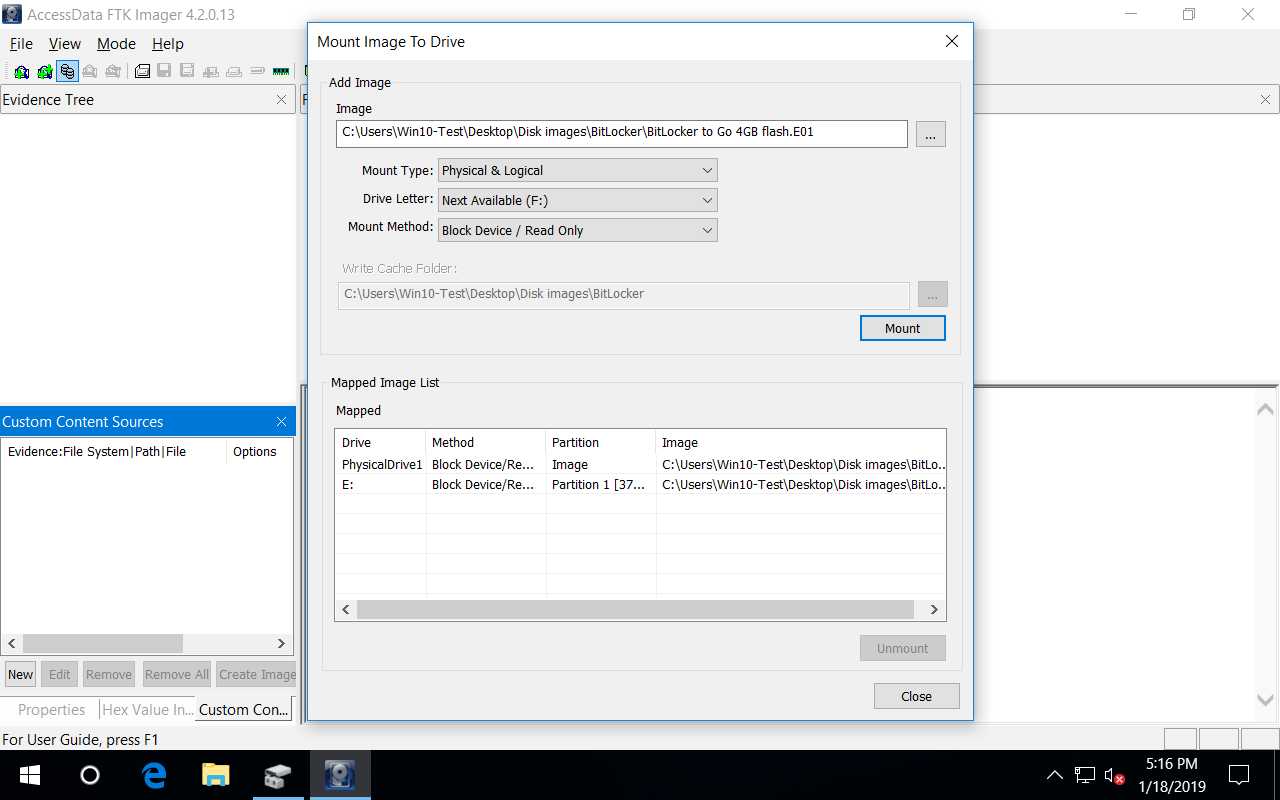
Ftk imager lite can produce all the following image formats except which one-Add the image as an Evidence item, using the File Menu (FTK Imager allows you to add evidence from physical volumes, logical volumes, image files, and folders) i You will select Image File and browse to find the image ii Load the image and explore it 1 Find two deleted files and export them to your machine Hi All, I'm currently using FTK Imager 3405 and trying to image a User Profile from a Mounted HDD which is Bitlocker Encrypted Once mounted and decrypted I have access to the drive and launch FTK imager, selecting the Contents option The image then starts and fails around 25 mins with the Errors during AD1 Creating message




Ftk Imager And Custom Content Images Salt Forensics
Pg23 1 FTK imager can produce all the following image formats except?eve 2 which of the following features isn't available in FTK Imager?Navigate to FTK Imager Lite Instructions Place the following URL into the address textbox and press enter (See Picture) http//wwwaccessdatacom/support/productdownloads;Download ftk imager lite for free System Utilities downloads AccessData FTK Imager by AccessData Group, LLC and many more programs are available for instant and free download
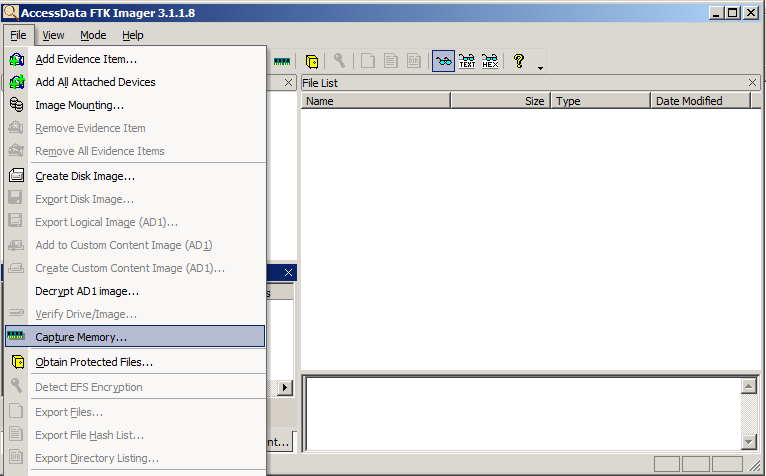
Release Information Imager 342 can read AD1 images created by previous version of Imager, but AD1 images created by Imager 343 can only be read by FTK, Summation, and eDiscovery version 6x and later Release NotesOnce the item is added to the evidence, you can perform the process of creating a forensic image FTK Imager allows you to make several different types of forensic images In addition, drive content and hash lists can be exported To create the image, perform the following steps Click on theCapturing an Image with AccessData FTK Imager Lite (1 of 8) • Included with AccessData Forensic Toolkit • Designed for viewing evidence disks and disktoimage files • Makes disktoimage copies of evidence drives • At logical partition and physical drive level • Can segment the image file • Evidence drive must have a hardware write
The FTK Imager has the ability to save an image of a hard disk in one file or in segments that may be later reconstructed It calculates MD5 hash values and confirms the integrity of the data before closing the files In addition to the FTK Imager tool can mount devices (eg, drives) and recover deleted files PreRequisite FTK Imager LessonRAM Acquisition with FTK imager and Volatility This RAM acquisition guide will work on all current versions of Windows, including Windows Server However, not all volatility commands are compatible with each version of Windows Volatility is a CLI tool for examining raw memory files from Windows, Linux, and Macintosh systems Download or reinstall FTK Imagerexe It is not recommended to download replacement exe files from any download sites, as these may themselves contain viruses etc If you need to download or reinstall FTK Imagerexe, then we recommend that you reinstall the main application associated with it Forensic Toolkit So, please do not try to consider it as a ranking of



Module 02 Ftk Imager




Image Formats Computer Forensics With Ftk
Forensics ToolKit Imager The FTK Imager is a simple but concise tool It saves an image of a hard disk in one file or in segments that may be later on reconstructed It calculates MD5 hash values and confirms the integrity of the data before closing the filesBeing optimised to search large volumes of data Creating eve images 3 FTK Imager Lite is designed to be portable, True or FalseAdd All Attached Devices Image Mounting Remove Evidence Item View files in hex format Open FTK Imager User Gu de AccessData FTKImager 31Ig File View Mode Help Evidence Tree Hex Value Interpreter x File List ified Select Drive Source Drive Selection Please select from the following available drives HITACHI HTSE630 50CG8




Using Ftk Imager To Create A Disk Image Of A Local Hard Drive 1337pwn




Module 02 Ftk Imager
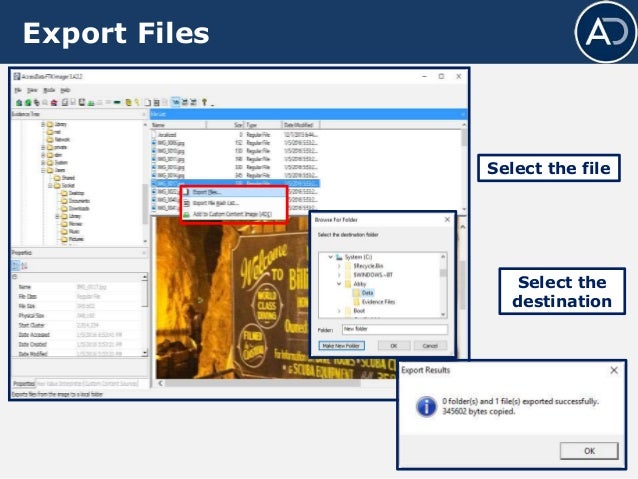
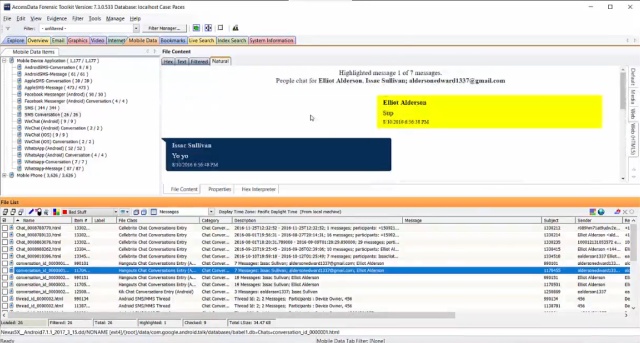
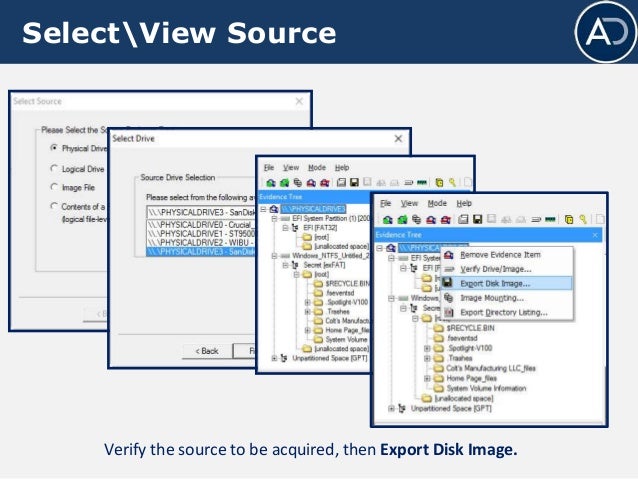
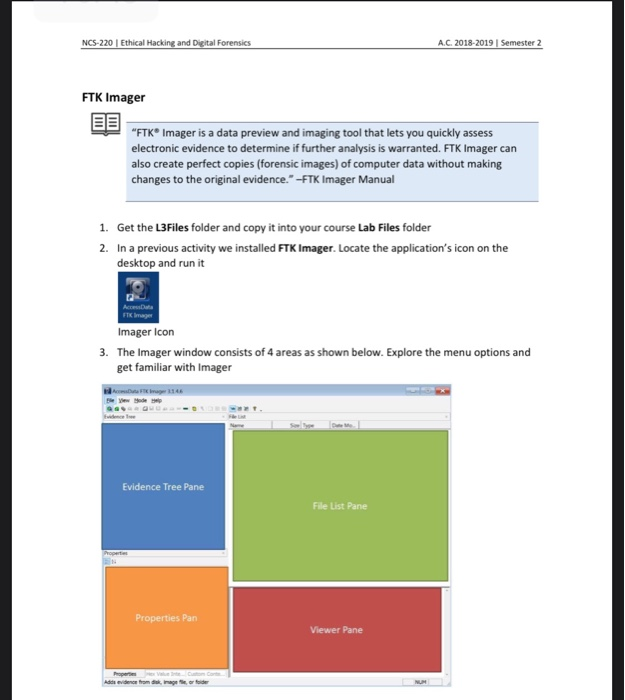
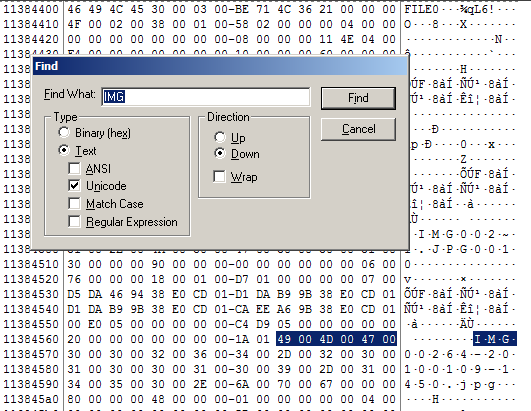
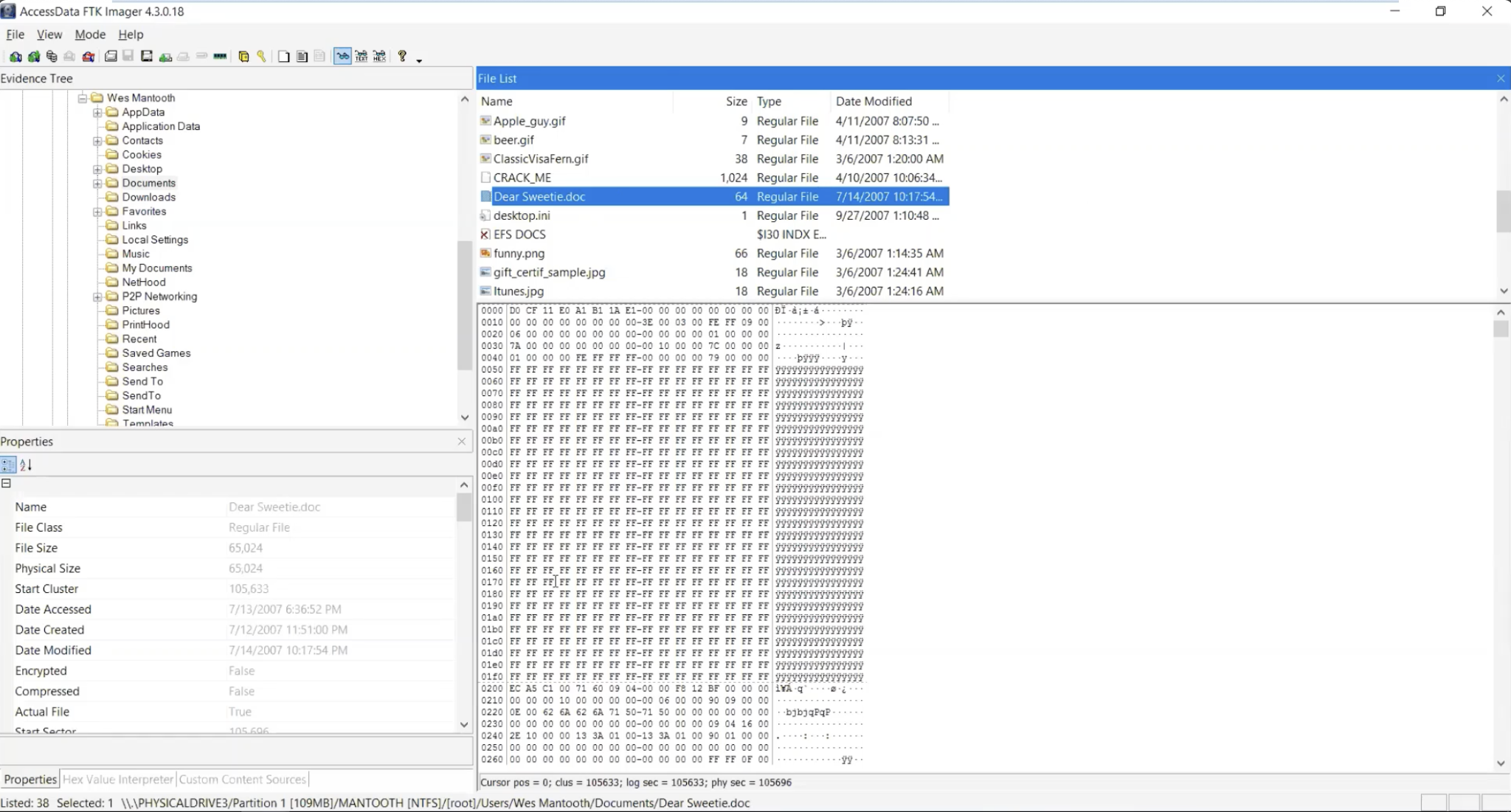
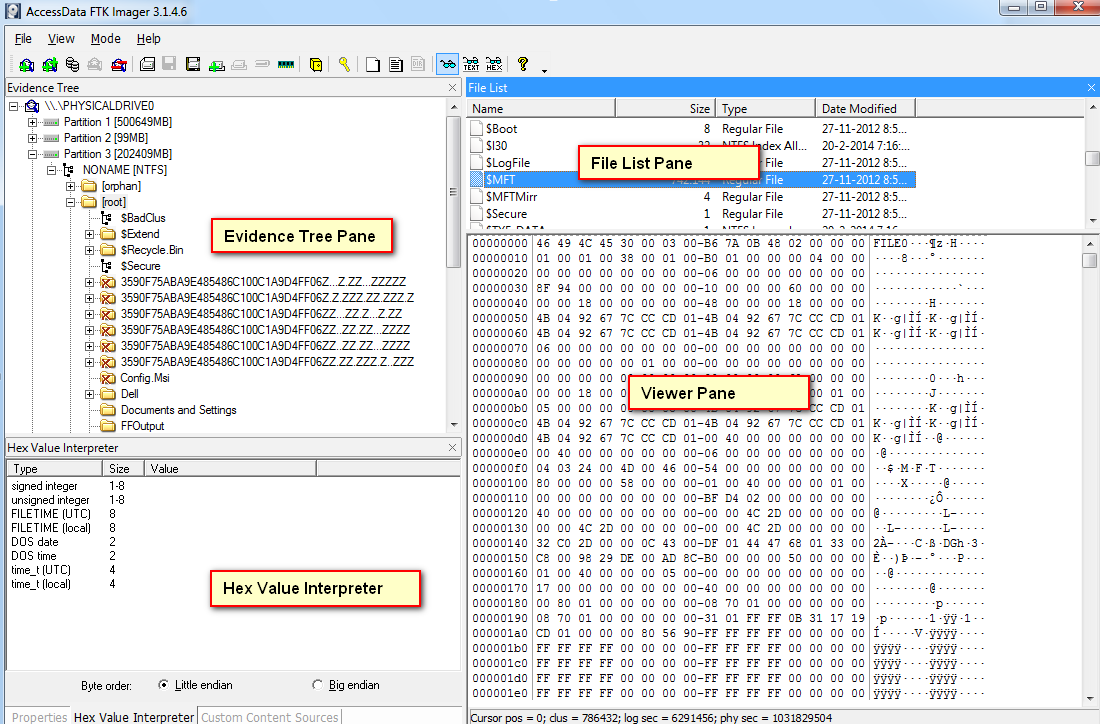
Create an Image Using FTK Imager I'm going to create an image of one of my flash drives to illustrate the process To create an image, select Create Disk Image from the File menu Source Evidence Type To image an entire device, select Physical Drive (a physical device can contain more than one Logical Drive) As previously stated, this same tool can be used to collect a disk image as well Open FTK Imager and navigate to "Create Disk Image" Now select the source that you need to acquire NOTE FTK Imager is capable of acquiring physical drives (physical hard drives), logical drives (partitions), image files, contents of a folder, or CDs/DVDs Investigators can connect Figure 1 FTK Imager Panes SEARCH FOR INTERESTING FILES Click the Viewer Pane and press the CTRL F keys to open up the Find function Search for pictures and perhaps decide to enter the common term "IMG" Figure 2 Search for file artifacts in the MFT (FTK) In a short while FTK Imager finds a result In this case, the search hit belongs to a file named



Forensic Analysis Using Ftk Imager




Ftk Imager For Mac Notever
Click on FTK IMAGER; To view the image, open up FTK Imager and click on "add evidence item" and select your image file Now you have an evidence item in the form of the image of the USB drive FTK Imager an "export hash list" feature, which can be used to export a list of the hashes (MD5 and SHA1 respectively) of all the files on the image 1 Install Latest Version Of FTK Imager Ensure that you have the latest FTK Imager software installed from AccessData's official site 2 Start FTK Imager From Your Windows PC On your Windows PC, doubleclick the icon labelled "AccessData FTK Imager" FTK Imager will start 3 Add Physical Drive As Evidence Item ("File" > "Add Evidence Item")



2



2
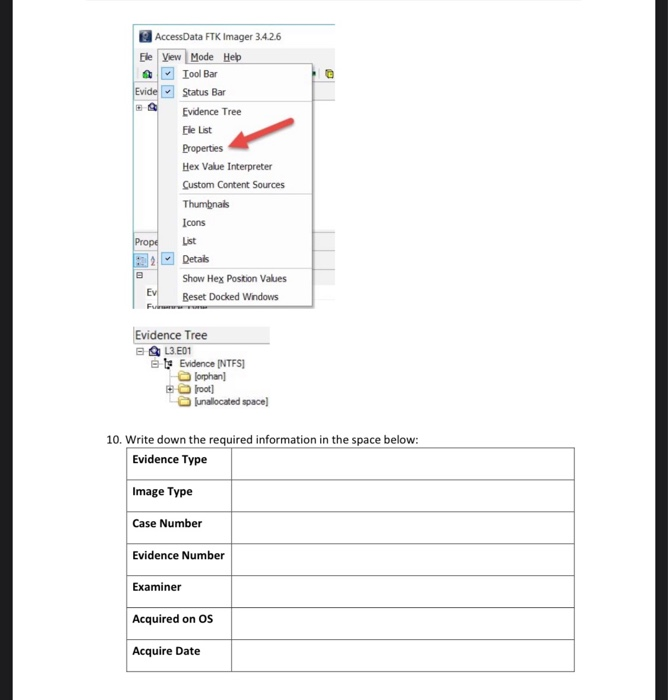
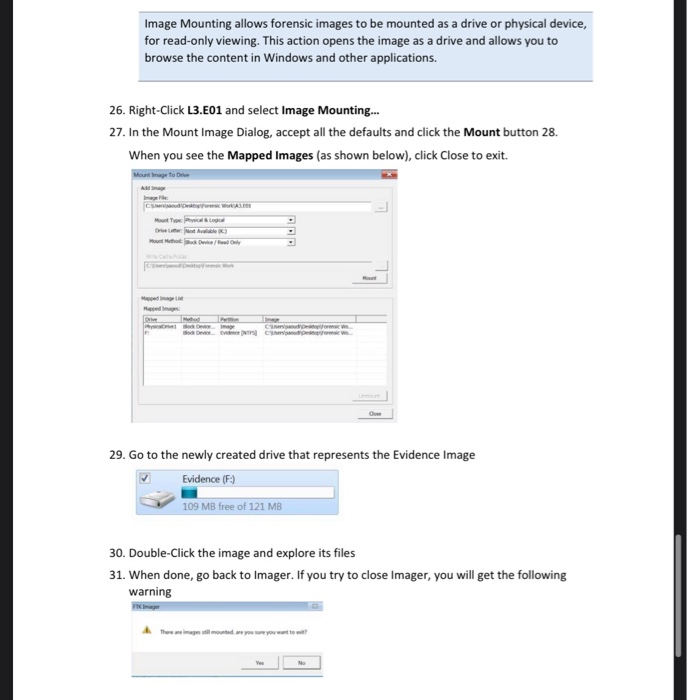
CardsReturn to Set Details When previewing a physical drive with FTK Image, you observe 3 logical volumes numbered 1, 2 & 5 Explain the drive numbering system Name six file systems that can be read by FTK Imager List the four types of evidence you can add to FTK Imager Yes As with nearly all programs in Linux there is a help file that allows the user to see what options are available and the proper syntax Unfortunately ftkimager does not have a man or info page so we will have to settle with the help file You can access the help file by either typing a wrong syntax after ftkimager OR you can type the following syntax sudo ftkimager –help andThis course, FTK Imager OnDemand Training, will guide users through the features and processes necessary to use FTK Imager This course covers the process of creating a forensic image in various formats, viewing evidence using FTK Imager, and the triage process for gathering evidence from live machines




Defcon Dfir Ctf 18 Writeup Or10n Labs



Ftk Imager Image Creation And Autopsy Analysis Youtube
Select one or more files (use CtrlClick to select multiple files or ShiftClick to select a range of files), then rightclick on one of the files to display a popup menu Select Export Files to export the selected files, then FTK Imager will prompt you for a folder where the files will be saved The files will be saved to that folderA friend helped me create an FTK Image of a friends hard drive (HFS) Mac drive and I can't open it Any tips, ideas, or help of any kind would be great I don't know if this helps at all, but the drive that was imaged was a hybrid SSDHDDSave FTK IMAGER LITE Instructions Click the Save File radio button;



Ftk Imager Lesson 2 Create Virtual Hard Drive Delete File Recover File




Forensics 101 Ram Capture Ftk Imager Raedts Biz It Security Forensics
Click the FTK Imager Lite version 311 Download Link ; Image 11 Full command to run FTK Imager Where 1 /dev/sdb – Is the source, the disk to acquire the image 2 /home/Ubuntu/Desktop/Folder/image – The destination of forensic image files, Folder is where the files will be storage, image is the name of the file 3 e01 – The format of the image, this kind is for Encase image file format 4 When you get to the Downloads folder you can use the ls command to view all of the files in that directory (On a side note I use the words directory and folder interchangeably when dealing with Linux, which they are) Determine what the FTK download is named, usually "ftkimagerxxx_UbuntuXXtargz where xxx stands for the version number



How To Create An Image Using Ftk Imager Ediscovery Best Practices Cloudnine




Ftk Imager Drive Selection Screen Download Scientific Diagram
FTK ® Imager Lite 31 1 FTK ® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence Export files and folders from forensic imagesFTK ® Imager 342 FTK ® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findingsO E01 (Expert Witness) o dd (raw) o S01 (SMART) o Ext4 (Linux) 2 Which of the following features isn't available in FTK Imager Lite?




The Ftk Imager Interface Computer Forensics With Ftk




Acquiring Memory Using Ftk Imager Learning Network Forensics
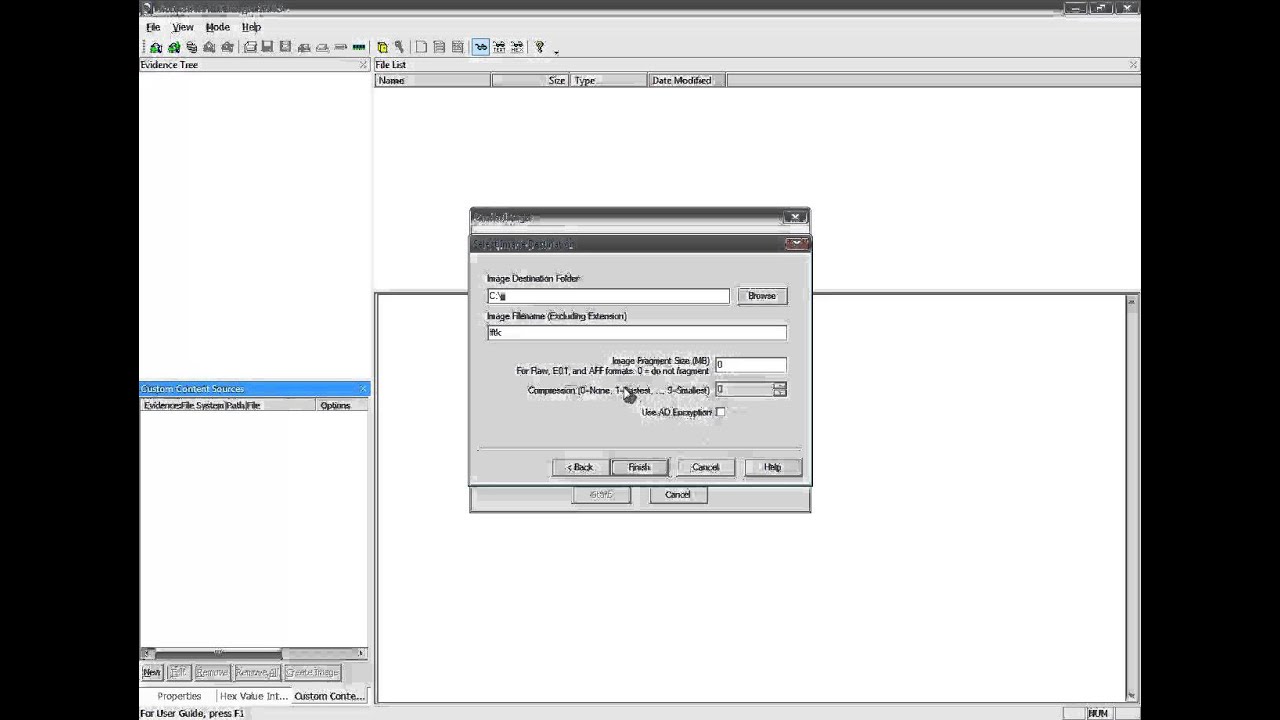
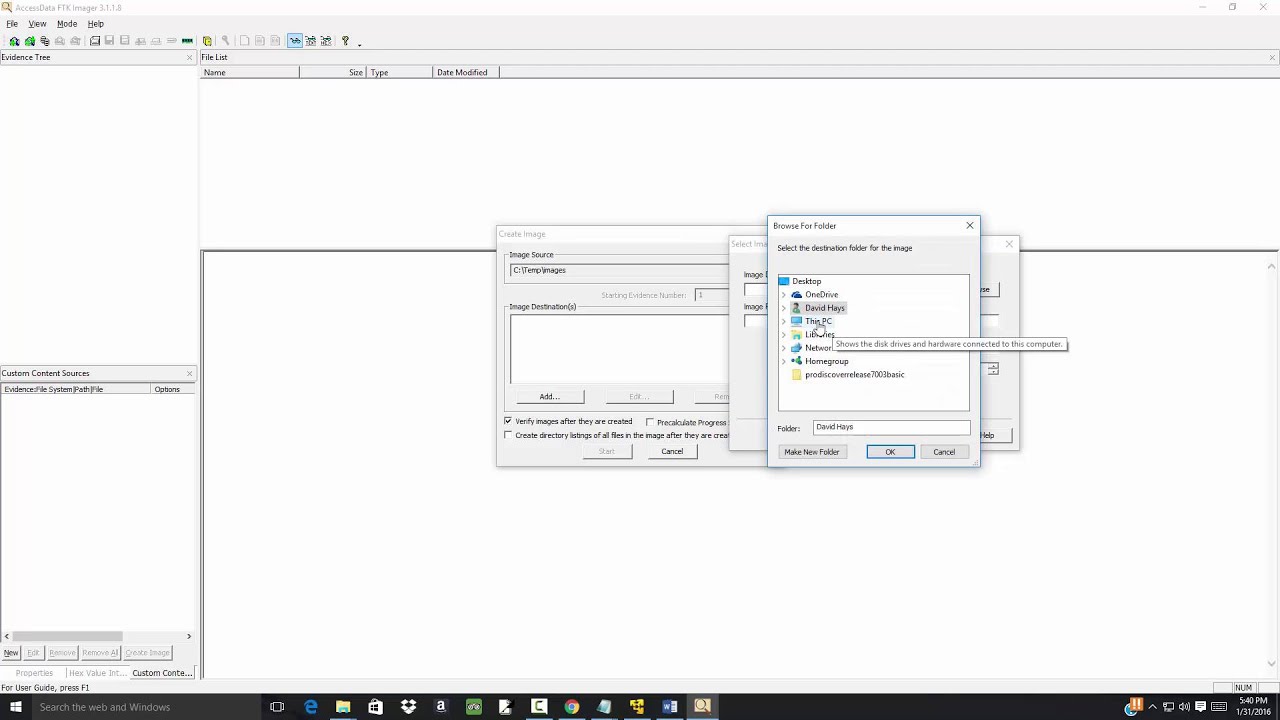
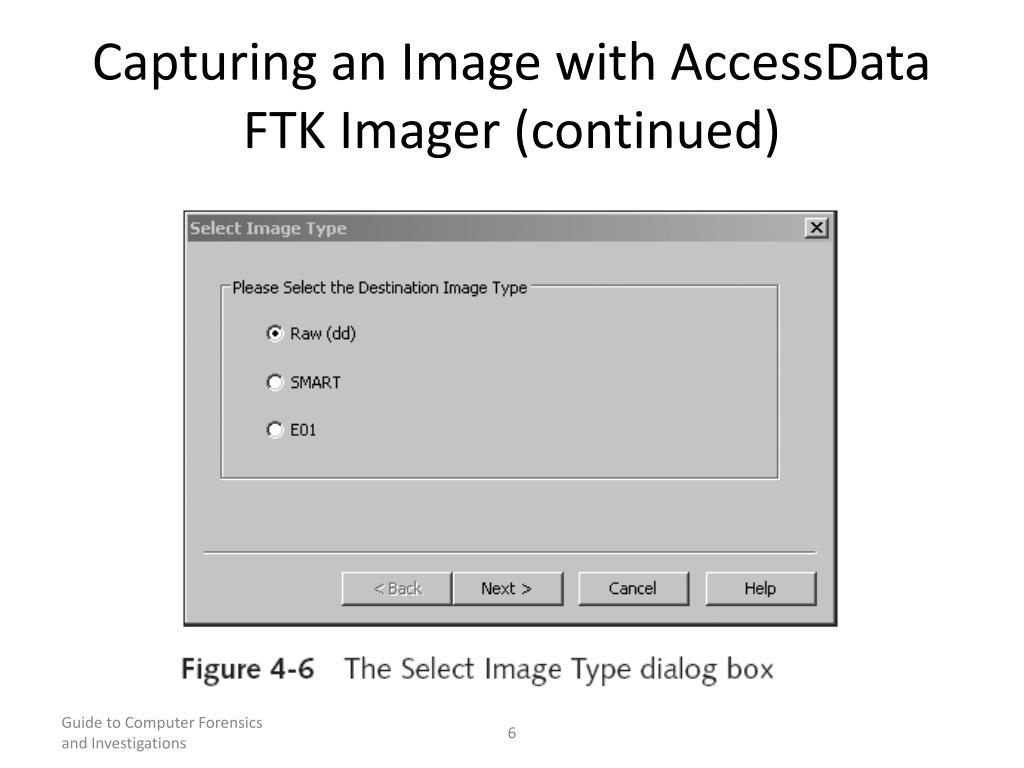
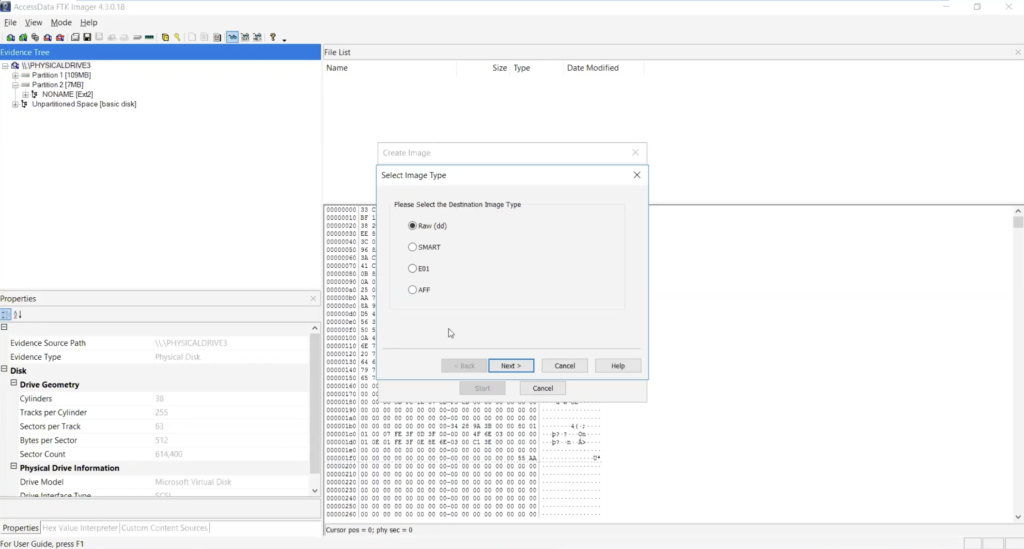
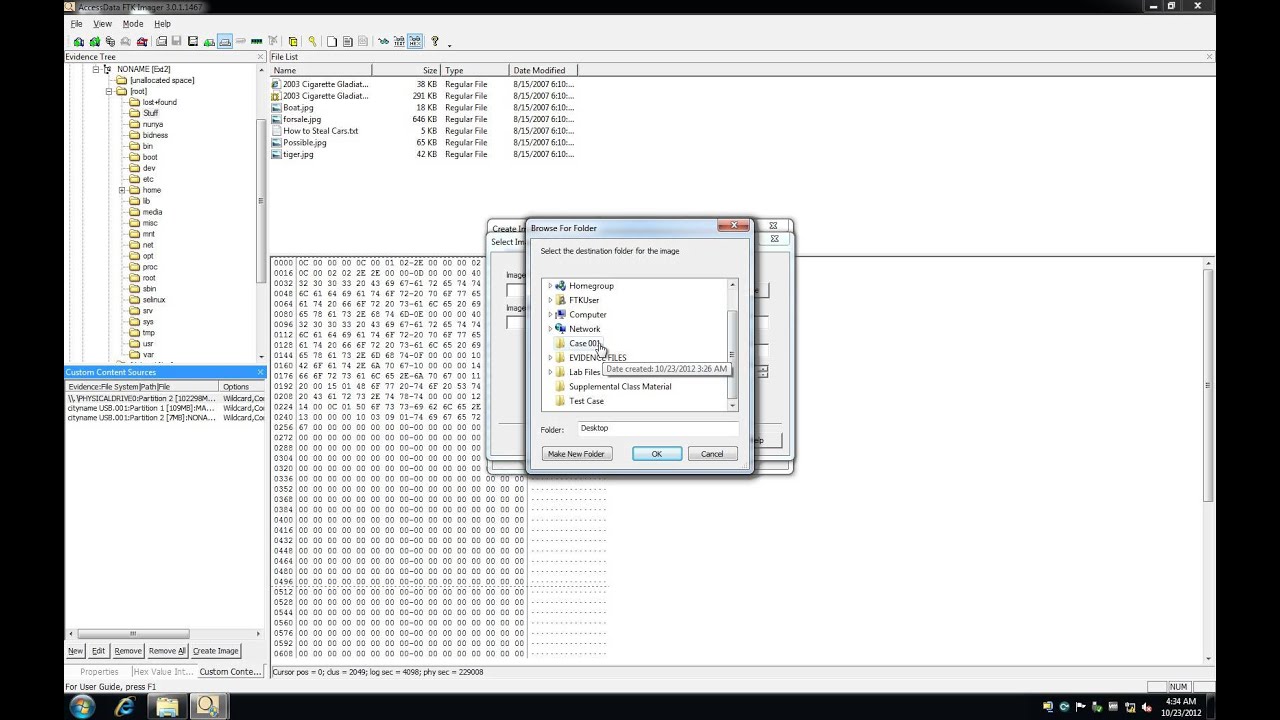
Next, select the image type The type you choose will usually depend on what tools you plan to use on the image The dd format will work with more open source tools, but you might want SMART or E01 if you will primarily be working with ASR Expert Witness or EnCase, respectively If your version of FTK requests evidence information, you can provide it If you select raw (dd) format, the image meta data will not be stored in the image file itself Select the ImageConnect the external HDD into the target system that has FTK Imager Command Line folder residing on it; Ftk imager lite can produce all the following image 1 FTK Imager Lite can produce all the following image formats except which one?




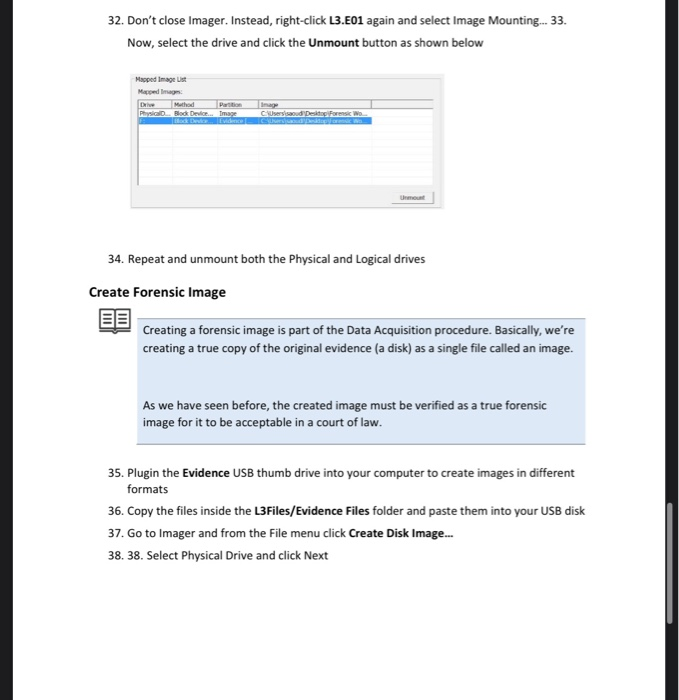
Ftk Imager State Machine Diagram Download Scientific Diagram




Multiple Ways To Create Image File For Forensics Investigation
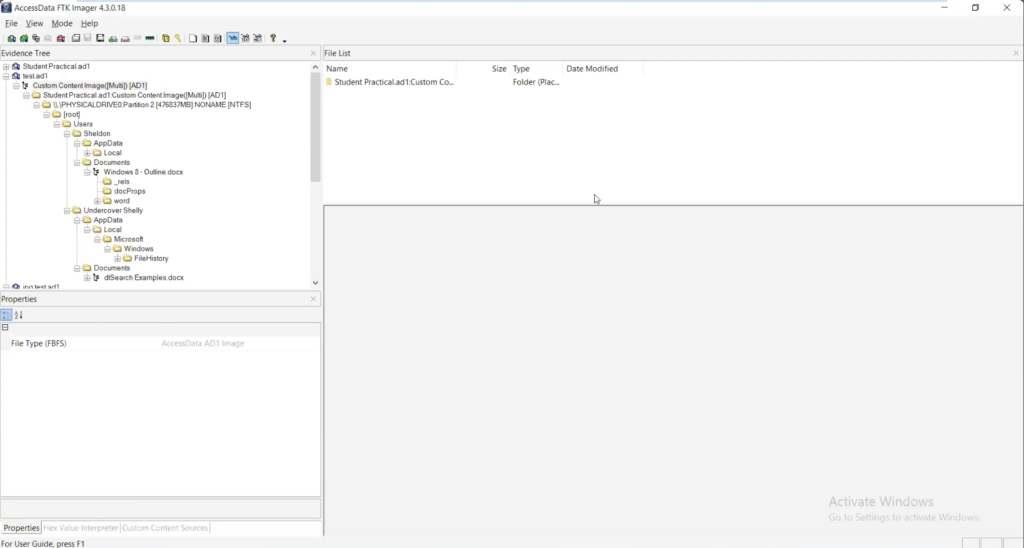
Academiaedu is a platform for academics to share research papers To do this, you must launch FTK Imager and then click File → Add Evidence Item → Image file and then click on your image To extract Registry files you must search in the directory at the path %SystemRoot%\System32\Config, rightclick on the file you need them and then select the export option Figure 246Click the OK button



Forensic Toolkit Ftk Accessdata



Introduction To Computer Forensics Ftk Imager Lite Creating An Image File Youtube
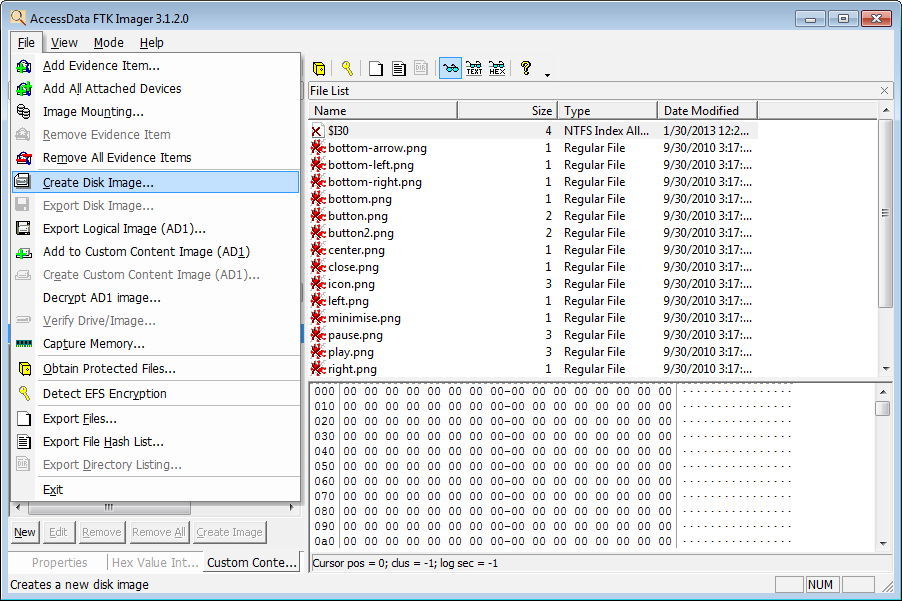
Click On "File" > "Create Disk Image" In the FTK Imager program, click on "File" We see that there are numerous options for creating images Let's select "Create Disk Image" 4 Select "Logical Drive" In "Select Source" Window Keep in mind that the proper drive type will depend on the circumstancesO Creating images in raw and E01 formats o Being optimized to search large volumes of data o Creating AFF image files o Extracting Windows Registry files© 19 Cengage May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or




Forensic Toolkit Ftk Accessdata




Ftk Imaging Step By Step By Parves Kamal Issuu
FTK ® Imager 311 FTK ® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findingsTake notes on the information about the affected To create a forensic image with FTK imager, we will need the following FTK Imager from Access Data, which can be downloaded using the following link FTK Imager from Access Data;




Using Ftk Imager For Mablab Nlwmablab




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna
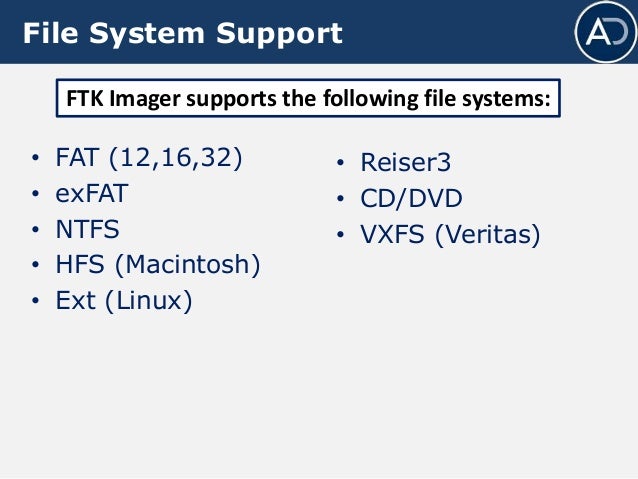
The Forensic Toolkit Imager (FTK Imager) is a commercial forensic imaging software package distributed by AccessData FTK Imager allows a forensic investigator to acquire physical device images and logically view data from FAT, NTFS, ext2, ext3, HFS, and HFS file systems Figure 21 shows the main FTK Imager screen Mount Image ProThe ftk imager can command line utility can be downloaded from the access data's webpage At the time of this writing, the link was the latest v ersion of ftk imager command line utilityAccessData FTK Imager, Version , was tested under a few testing scenarios to acquire bitforbit content of electronically stored information (a process known as "imaging") from select hard disk drives containing known content The tests were performed using the NIST CFTT Program digital forensics tool testing framework



Module 02 Ftk Imager



Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com
Select the device, taking care that you are choosing the correct one Now that you have selected the source, FTK Imager requires you to specify the destination location and format Click the Add button, shown below, and FTK Imager will walk you through adding a new destination You can specify more than one destination as well as different formatsIf you wish you can click on "Print" and print the test page) (3 When you want to take a testclick on anyone of the tests for that Study Set) (4 Click on "Check Answers" and it will score your test and correct your answers) (5 You can take all the tests as Using command line FTK Imager (for 32 bit Windows System) If you are trying to image 32 bit Windows System, you will need to use FTK Imager Command Line Login with a local admin account on the target system;




Ppt Ftk Imager 2 6 1 Powerpoint Presentation Free Download Id



2




Ftk Imager Lite Mayfasr




Ftk Imager Step By Step Eforensics



Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium



Module 02 Ftk Imager




Ftkimagerug Imager 2 9 0 User Guide




7 In The Select Image Destination Dialog Box Click The Browse Button Navigate Course Hero




Introduction To Computer Forensics Accessdata Ftk Imager 3 1 1 Opening An Image File Youtube



Ppt Hands On Capturing An Image With Accessdata Ftk Imager Powerpoint Presentation Id




Why Do Forensics Investigators Work With Bit Stream Images J An Image File Can Course Hero



Module 02 Ftk Imager




Reporting The Case Computer Forensics With Ftk




Digital Forensics Tutorials Acquiring An Image With Ftk Imager Pdf Free Download



Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com



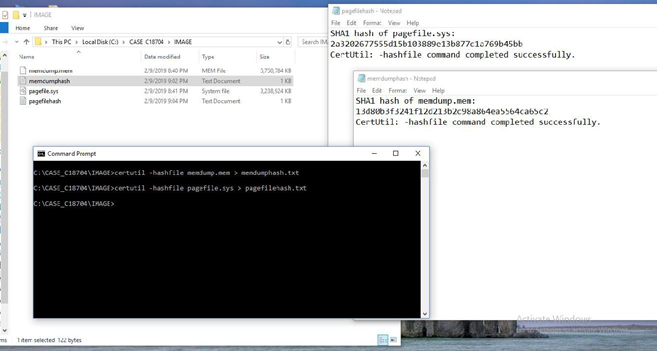
Project 3 Capturing A Ram Image 15 Points




Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium



Crear La Imagen Forense Desde Una Unidad Utilizando Ftk Imager Alonso Caballero Reydes




5 Forensics Investigators Should Be Familiar With More Than One Forensics Course Hero



Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com



What The Tech Using Ftk Imager Forensic Focus



Forensic Analysis Techniques




Comprehensive Guide On Ftk Imager



How To Investigate Files With Ftk Imager Eforensics



What The Tech Using Ftk Imager Forensic Focus



Restore File With Ftk Imager Youtube



Module 02 Ftk Imager




Ftk Imager Drive Selection Screen Download Scientific Diagram




Processing Files And Folders With Ftk Imager Digital Detective Knowledge Base Netanalysis



2



Capturing Memory And Obtaining Protected Files With Ftk Imager Ediscovery Best Practices Cloudnine



Github Mrmugiwara Ftk Imager Osx Ftk Imager A Forensics Tools For Mac Os X



2




Ftk Image Loading And Analysis Youtube



How To Investigate Files With Ftk Imager Eforensics



1




How To Perform A Physical Acquisition On An Sd Card Using A Forensic Tool



Features Of Working With Images Of Encrypted Disks In Windows



What The Tech Using Ftk Imager Forensic Focus




Acquiring Memory Using Ftk Imager Learning Network Forensics



Project 3 Capturing A Ram Image 15 Points




Ftk Imager For Mac



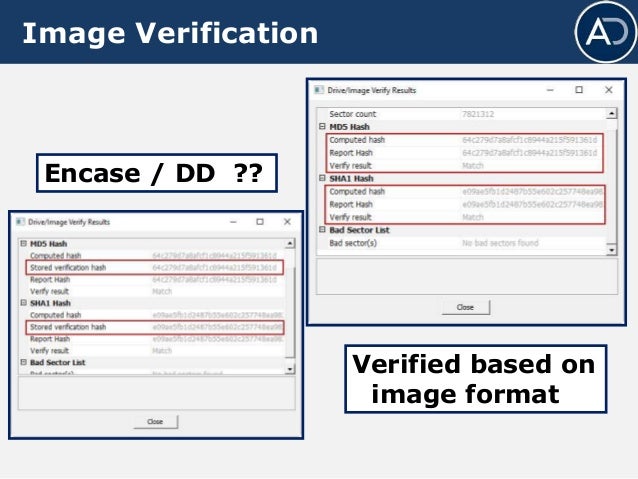
Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com




Forensic Image Analysis Of A Usb Drive



Module 02 Ftk Imager



Accessdata Ftk Imager Latest Version Get Best Windows Software




7 In The Select Image Destination Dialog Box Click The Browse Button Navigate Course Hero




Forensic Toolkit Ftk Accessdata




Comprehensive Guide On Ftk Imager



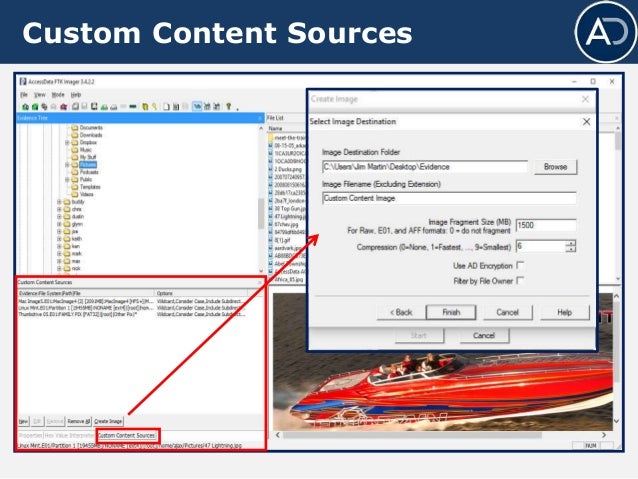
Ftk Imager And Custom Content Images Salt Forensics
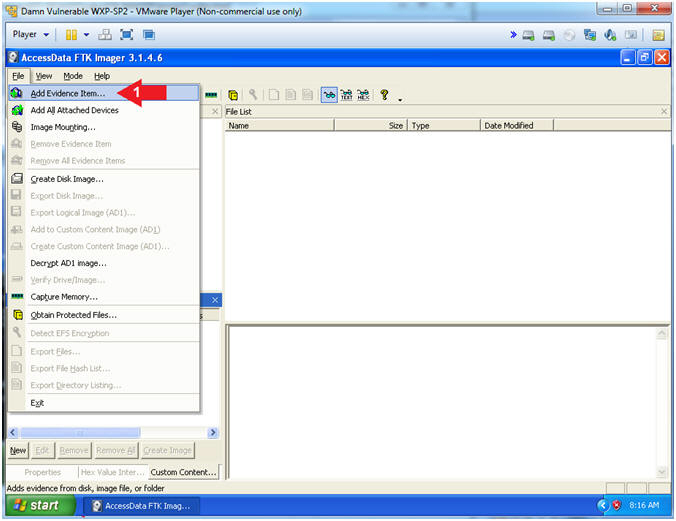



Ftk Imager Lesson 2 Create Virtual Hard Drive Delete File Recover File




A Dogged Pursuit Capturing Forensic Images Of 3 5 Floppy Disks Practical Technology For Archives




Ftk Imager And Custom Content Images Salt Forensics
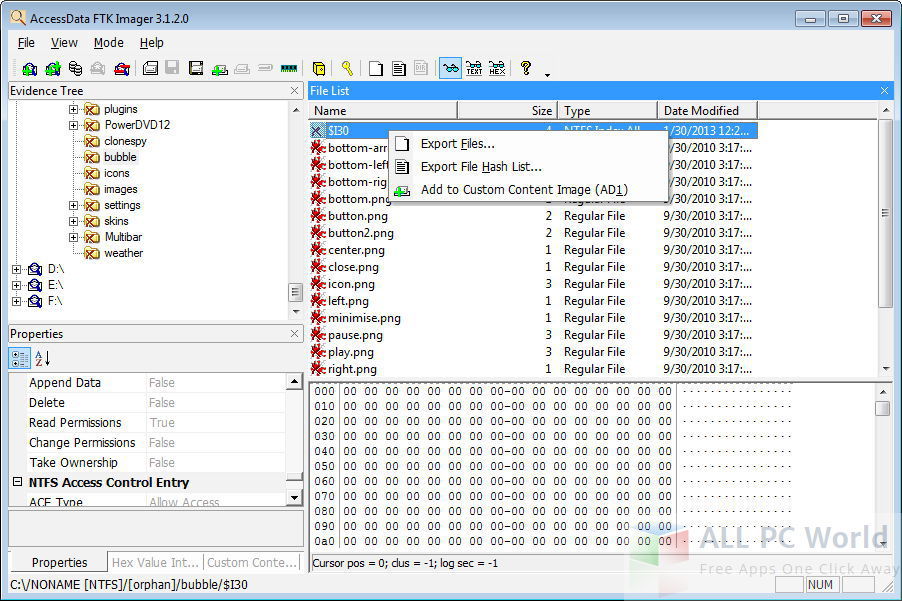



Forensic Toolkit Ftk Imager Free Download All Pc World



Ftk



Ftk Imager




How To Use Ftk Imager To Recover Data 1337pwn




Autopsy Vs Ftk Imager Manson Bryan S Itec 6322 Portfolio




Imaging Free Space Only Software Recommendations Stack Exchange
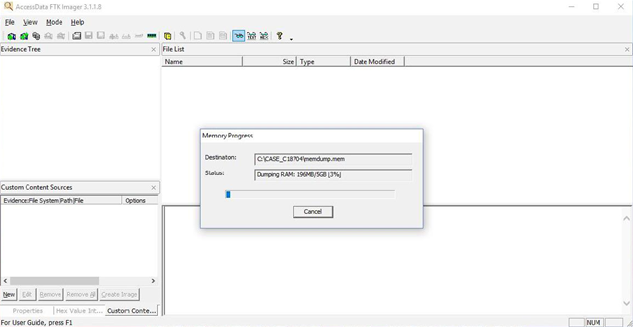



Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium




Digitalresidue S Forensics Memory Acquisitions Memoryze Ftk Imager Sleuthkit Etc




Using Ftk Imager To Create A Disk Image Of A Local Hard Drive 1337pwn




Digitalresidue S Forensics Memory Acquisitions Memoryze Ftk Imager Sleuthkit Etc




Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com



2




Using Ftk Imager To Find File Artifacts In Master File Table 1337pwn



Ftk
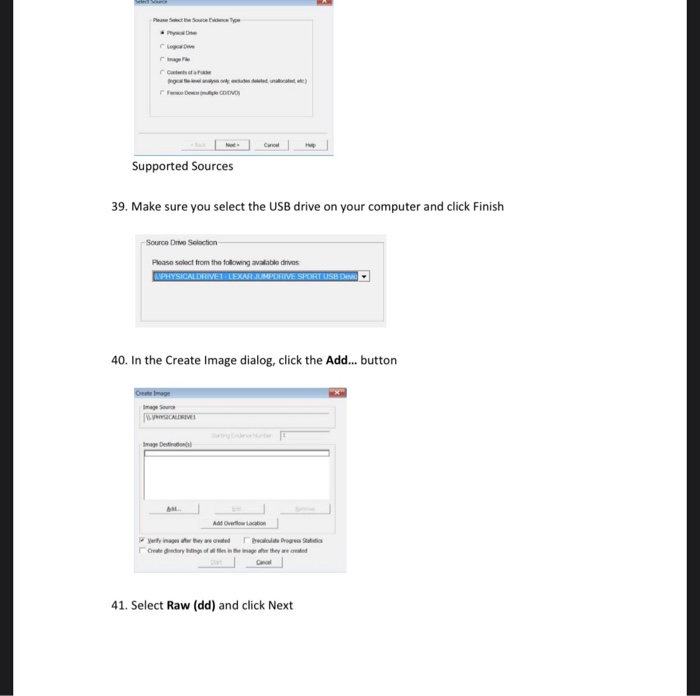



Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com



Solved Task 1 Basic Imaging Ftk Imager Task Objectives Chegg Com




Autopsy Vs Ftk Imager Manson Bryan S Itec 6322 Portfolio




Autopsy Vs Ftk Imager Manson Bryan S Itec 6322 Portfolio



2
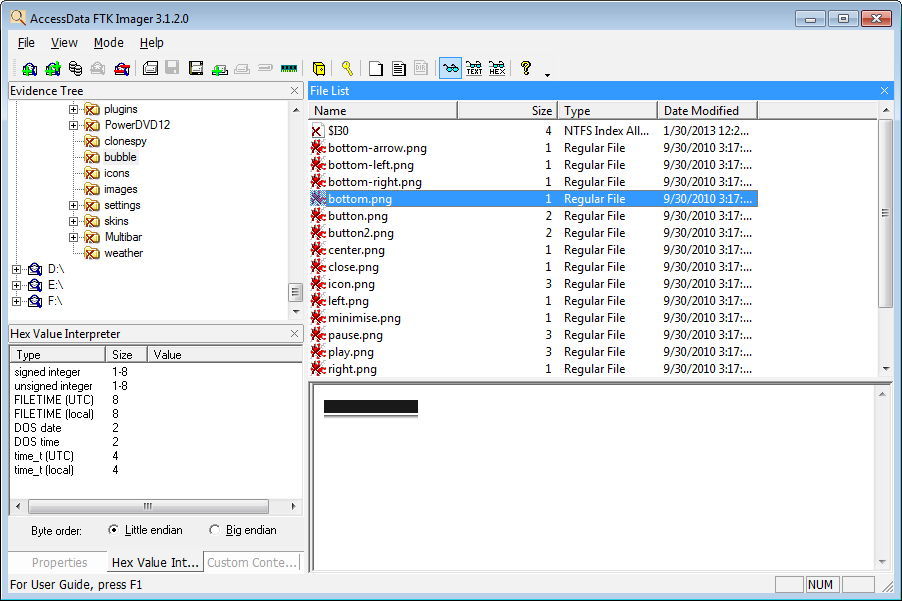



Accessdata Ftk Imager Latest Version Get Best Windows Software



Project 3 Capturing A Ram Image 15 Points
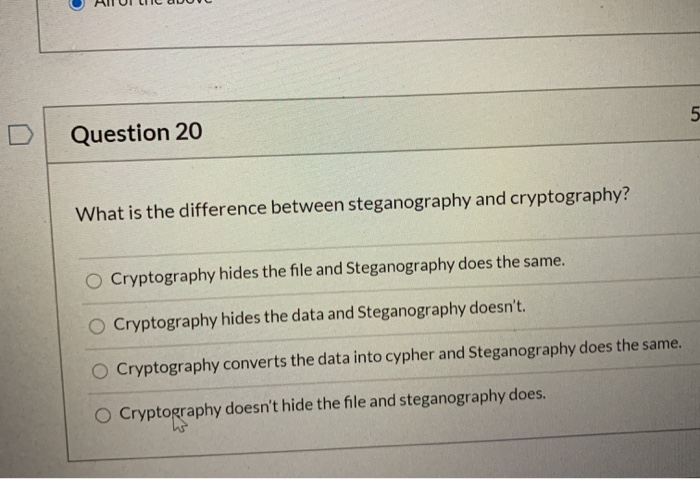



Solved Ftk Imager Is A Forensics Tool That Allows You To Chegg Com
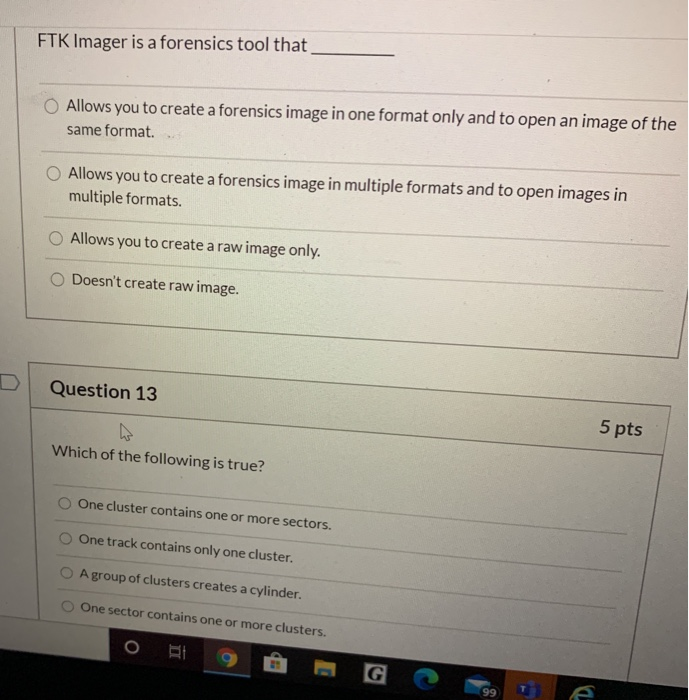



Solved Ftk Imager Is A Forensics Tool That Allows You To Chegg Com
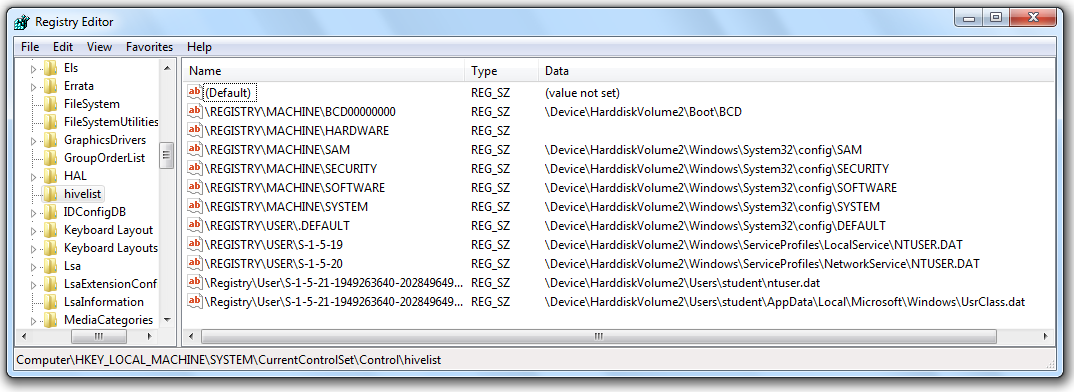



Project 17 Capturing And Examining The Registry 30 Pts
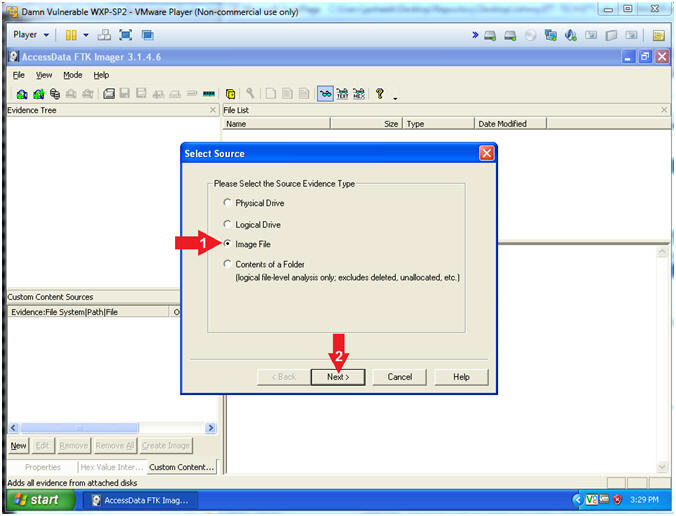



Ftk Imager Lesson 4 Mount Image File Recover Deleted File



0 件のコメント:
コメントを投稿